ABSTRACT
Future fifth-generation (5G) cellular systems are set to give a strong boost to the large-scale deployment of Internet of things (IoT). In the view of a future converged 5G-IoT infrastructure, cellular IoT solutions such as narrowband IoT (NB-IoT) and device-to-device (D2D) communications are key technologies for supporting IoT scenarios and applications. However, some open issues still need careful investigation. An example is the risk of threats to privacy and security when IoT mobile services rely on D2D communications. To guarantee efficient and secure connections to IoT services involving exchange of sensitive data, reputation-based mechanisms to identify and avoid malicious devices are fast gaining ground.
In order to tackle the presence of malicious nodes in the network, this paper introduces reliability and reputation notions to model the level of trust among devices engaged in an opportunistic hop-by-hop D2D-based content uploading scheme. To this end, social awareness of devices is considered as a means to enhance the identification of trustworthy nodes. A performance evaluation study shows that the negative effects due to malicious nodes can be drastically reduced by adopting the proposed solution. The performance metrics that proved to benefit from the proposed solution are data loss, energy consumption, and content uploading time.
RELATED WORK
Security is one of the key issues for an effective and widespread adoption of D2D communications in IoT scenarios. This is particularly relevant in a cooperative context such as the one studied in this paper, where the multihop D2D data forwarding paradigm is based on the assumption that the involved devices behave in a trusted and secure way. Unfortunately, this is not always the case as malicious nodes may be active in the network by either dropping or manipulating the data to be forwarded.
NB-IOT AND D2D COMMUNICATIONS IN THE 5G ERA
The upcoming fifth generation (5G) wireless systems are being considered as the best candidate to allow effective interworking of IoT devices, thanks to the benefits these offer in terms of enhanced coverage, high data rate, low latency, low cost per bit, and high spectrum efficiency. There is a general consensus among academia and industries that 5G will have a huge impact in three main areas of communication: (1) enhanced mobile broadband (eMBB); (2) massive-machine type communication (M-MTC); and (3) critical-MTC (c-MTC).
COOPERATIVE MULTIHOP D2D-BASED DATA UPLOADING
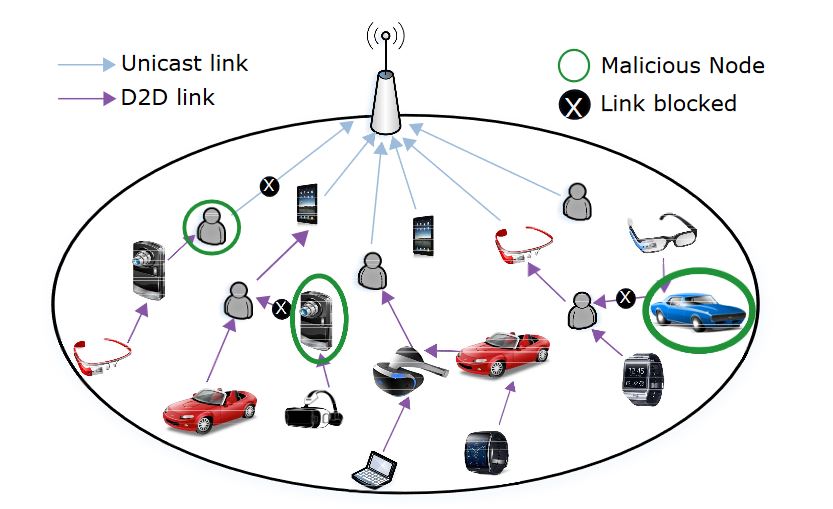
Figure 1. Cooperative multihop content uploading based on trustworthy device to device (D2D) links
To cope with the threats coming from the malicious nodes, when defining the cooperative topologies, countermeasures must be considered to offer rational users the possibility to filter out untrusted users, block the unsecure links and avoid unsuccessful opportunistic hop-by-hop D2D interactions, as sketched in Figure 1. The solution we propose for effective and trusted D2D-based data uploading.
THE SOCIAL-AWARE TRUST MODEL
In our scenario the eNodeB acts as a trusted third party that implements the coalition formation model based on social-aware trustworthiness. To this aim, we evaluate the potential of the SIoT model to embrace the social networking concepts and build trustworthy relationships among the devices. The eNodeB will store information about the reliability, reputation and trust of the users in the network. We define a player trust matrix (PTM) as the data structure stored in the eNodeB containing information for every pair of devices. This information will be used whenever a new coalition formation is triggered.
PERFORMANCE EVALUATION
As we can observe from Figure 2, the proposed trust-based solution always performs better compared to the basic strategy (we consider here the sample case with FT = 0.5). In particular, when there is a prevalence of type A malicious nodes in the system we obtain lower benefits in terms of uploading time and energy consumption. The motivation behind this is that the energy consumed for a UE when receiving corrupted packets is added to the energy required to upload the content with a unicast link to the eNodeB.
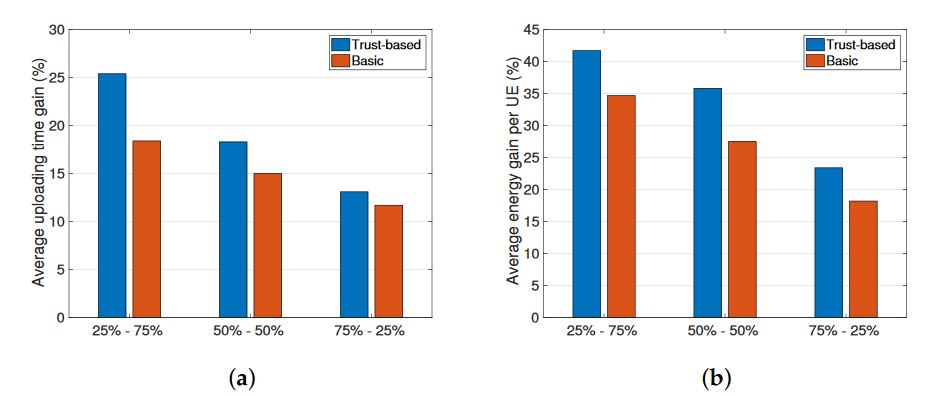
Figure 2. Impact of type A and type B malicious nodes (feasility threshold, FT = 0.5). (a) Uploading time gain; (b) Average energy gain
In Figure 4 results are presented when varying the FT value from 0.2 to 1.0, under the condition of 50% malicious nodes in the system. Interestingly, the gain achieved in terms of uploading time increases linearly with the value of FT until reaching a value of 31% (see Figure 4a). However, this result is obtained at the cost of a higher energy consumption for the nodes. As shown in Figure 4b, the energy consumption gain decreases with the FT and the proposed solution performs even worse than the basic one for FT values beyond 0.5.
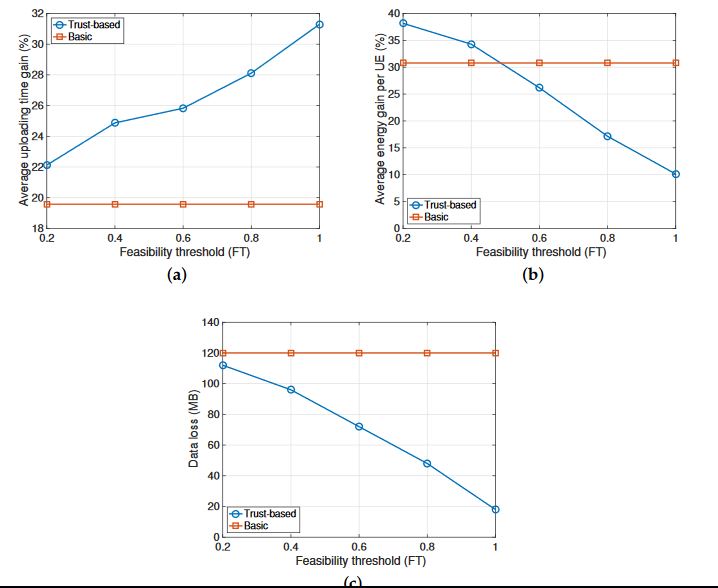
Figure 4. Impact of feasibility threshold (50% of malicious nodes, half of type A and half of type B). (a) Uploading time gain; (b) Average energy gain; (c) Data loss. UE: user equipment
CONCLUSIONS
In this paper we proposed a trust-based solutions for effective D2D-enhanced cooperative content uploading in narrowband-IoT cellular environments. To limit the impact of the malicious nodes either dropping or corrupting the data packets in a cooperative multihop coalition, social awareness has been modeled to evaluate the reliability for the nodes and to suitably weigh the recommendations exchange for the reputation definition.
A simulative analysis validated the proposed solution in a wide range of settings for small-scale IoT scenarios. The results showed how the social-based trusted solution guarantees higher gains in the content uploading time, in the energy consumption, and has the ability to increase the amount of successful cooperative interactions by filtering out the malicious nodes.
Source: University Mediterranea
Authors: Leonardo Militano | Antonino Orsino | Giuseppe Araniti | Antonio Lera
>> 200+ IoT Led Projects for Engineering Students
>> IoT based Networking Projects for Final Year Students
>> More Wireless Energy Projects for Final Year Students
>> More Wireless Mini Projects for Engineering Students